Chromebook RFP Parkway School
OBJECTIVE
The district is currently accepting proposals from vendors for the following model:
o Chromebook: Acer C-733T
The district may also purchase smaller quantities of Chromebook devices between May 1, 2021, and May 1, 2022.
The District requires delivery within 30 days of receipt for additional purchase orders to our warehouse at 363 N. Woods Mill Rd, Chesterfield, MO 63017.
Quantities are estimates and are listed as guidance in estimating volume pricing. The District does not guarantee any quantities that it will purchase as a result of this invitation for bid. Parkway is currently seeking a one-year agreement
MANDATORY REQUIREMENTS
Professional Services Requirements:
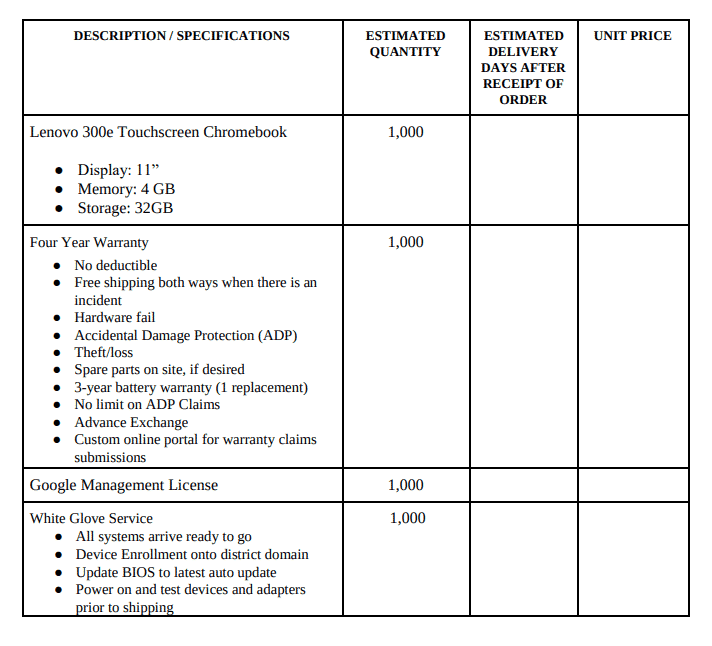
A. Setup Services
o Quantity: 7500
o Description: Setup services including domain registration. Many resellers provide “white glove” services that include registering the Chromebooks in our G-Suite domain. This increases the ease and efficiency of deploying the devices. Parkway is looking for domain registration for all devices purchased, as well as the option for asset tagging.
B. Hardware/Software/Licensing Requirements:
o Chromebook Option: Acer C-733T
Quantity: 7500
Minimum Requirements:
Intel Processor
4GB RAM
16GB SSD
11.6” touch display
1-year warranty (minimum)
o Academic Google Chrome OS Management License
Quantity: 7500
Description: Academic Google Chrome OS Management License and Support for 5 years for GAFE
Domain: parkwayschools.net
C. Optional Requirements:
Professional Services Requirements: N/A
Hardware/Software/Licensing Requirements: Accidental/Extended Warranties – Please include a detailed description of warranty coverage, claim or repair process, average repair times, and any associated costs (including shipping). ∙ 3-year cost ∙ 4-year cost
SB-3 TIMETABLE:
Bid Publish Date 11/23/2020
Bid Close Date 12/14/2020 11:00 AM CST
Bid Questions Due by Date: 12/8/2020 By end of business day
Bid Questions Responses by: 12/11/2020 By end of business day
Location of Bid Opening: Online via Google Meets Bid Opening Link: meet.google.com/bdc-idzm-xzc
If interested contact Craig at catareno.com
Since 1999, Thinclient.org has been reporting the thin client computing market as well as the ChromeBook, Zero Client, Android clients, Pi Raspberry Clients and Thick Client market. Generally the cloud computing market since it started with companies such as Citrix back in the late 80s.
A thin client is a lightweight[vague] computer that has been optimized for establishing a remote connection with a server-based computing environment. The server does most of the work, which can include launching software programs, performing calculations, and storing data. This contrasts with a fat client or a conventional personal computer; the former is also intended for working in a client–server model but has significant local processing power, while the latter aims to perform its function mostly locally.
Thin client hardware generally supports a keyboard, mouse, monitor, jacks for sound peripherals, and open ports for USB devices (e.g., printer, flash drive, webcam). Some thin clients include legacy serial or parallel ports to support older devices such as receipt printers, scales or time clocks. Thin client software typically consists of a graphical user interface (GUI), cloud access agents (e.g., RDP, ICA, PCoIP), a local web browser, terminal emulators (in some cases), and a basic set of local utilities.
New hardware interfaces includes socket-based enabled devices eliminating the need for a physical USB connection. Bluetooth wireless connectivity is also a big factor for devices.